VBS/Jenxcus.H is a Trojan horse. If it accesses into your computer whatever unfair methods it uses, you will have many unnecessary troubles. First, it randomly download other programs into your computer without permission. Also, VBS/Jenxcus.H changes the settings of your computer stealthily, deleting some system files if it is needed. In this case, the stability of your computer system will turn weak.
WHat's worse, if there has something valuable in your computer, hackers can actually use this Trojan horse to get it easily. So, VBS/Jenxcus.H is high-risky infection. Now, let's remove it.
Remove VBS/Jenxcus.H Manually from Computer:
1. To stop all VBS/Jenxcus.H processes, press CTRL+ALT+DELETE to open the Windows Task Manager.
2. Click on the "Processes" tab, search for VBS/Jenxcus.H, then right-click it and select "End Process" key.
[random].exe
How to stop VBS/Jenxcus.H related processes
3. Navigate to directory of VBS/Jenxcus.H and delete the infected files manually.
%AllUsersProfile%\{random}
%AllUsersProfile%\Application Data\.dll
%AllUsersProfile%\Application Data\.exe
%ProgramFiles%\random.exe
4. Click "Start" button and selecting "Run." Type "regedit" into the box and click "OK."
5. Once the Registry Editor is open, search for the registry key "HKEY_LOCAL_MACHINE\Software\VBS/Jenxcus.H."
Right-click this registry key and select "Delete."
Remove VBS/Jenxcus.H with Spyhunter Antivirus program:
Manual removal requires expert skills in dealing with related program files, processes, .dll files and registry entries. If you're not familiar with that, it's recommended to download SpyHunter to help you to block it manually and previously.1: Click on the Download button and save its application into your computer.
2: Then a prompt box will pop up to ask you if you will run it, click Run and wait for its installation.
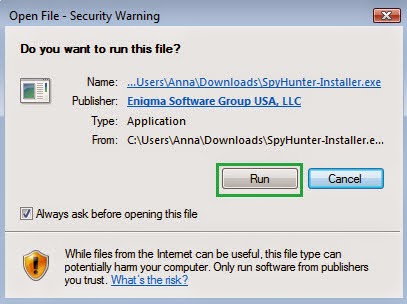
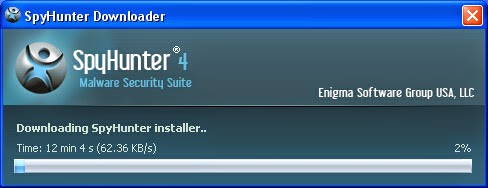
3: When it finishes installation, click on the Scan Computer Now button to begin scanning, when it displays the final report of detected threats, remove them.





No comments:
Post a Comment