VBS/Agent.NDH.5 is actually a backdoor Trojan horse. It can break inside your computer through those system vulnerabilities on your computer. Then, it will start a backdoor download to install lots of malicious programs and applications into your computer without permission.
VBS/Agent.NDH.5 is nasty. It can slow down your computer perform speed and affect your computer stability in a negative way. Sometimes, the situation can be worse. Your computer may be shut down for no reason.
Moreover, VBS/Agent.NDH.5 can technically be utilized for personal information collecting as long as it installs some malicious script or plug-ins into your computer. Anything if only you input in your computer can be recorded on purpose.
To safeguard your computer and precious data, you should get this VBS/Agent.NDH.5 removed from your computer as soon as possible. Follow this article, and I will show you two basic ways to get rid of VBS/Agent.NDH.5.

Method 1 to Remove VBS/Agent.NDH.5:
1. To stop all VBS/Agent.NDH.5 processes, press CTRL+ALT+DELETE to open the Windows Task Manager.
2. Click on the "Processes" tab, search for VBS/Agent.NDH.5, then right-click it and select "End Process" key.
[random].exe
3. Navigate to directory of VBS/Agent.NDH.5 and delete the infected files manually.
%AllUsersProfile%\{random}
%AllUsersProfile%\Application Data\.dll
%AllUsersProfile%\Application Data\.exe
%ProgramFiles%\random.exe
4. Click "Start" button and selecting "Run." Type "regedit" into the box and click "OK."
5. Once the Registry Editor is open, search for the registry key
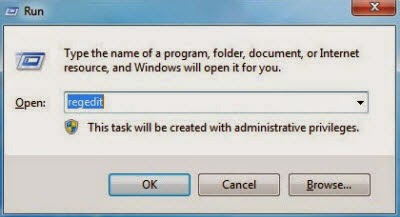
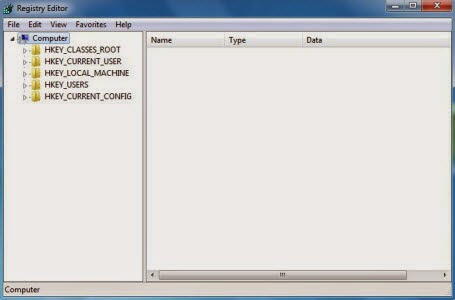
"HKEY_LOCAL_MACHINE\Software\VBS/Agent.NDH.5."
Right-click this registry key and select "Delete."
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Current Version\Run\random.exe"
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
HKEY_CURRENT_USER\AppEvents\Schemes\Apps\Explorer\Navigating
(Note: The posted instruction is recommended for advanced users only. A trying without any expertise will be at your own risk.)
Method 2 to Remove VBS/Agent.NDH.5:
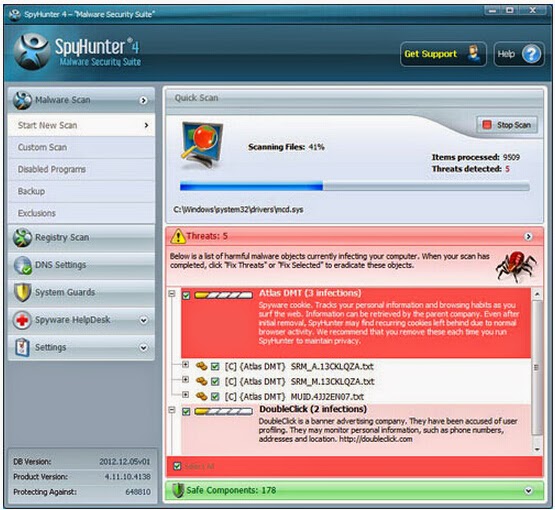
1. Download Spyhunter into your computer;
2. Once it been installed in your computer, you should run a full scan with it to find out any threat in your computer.
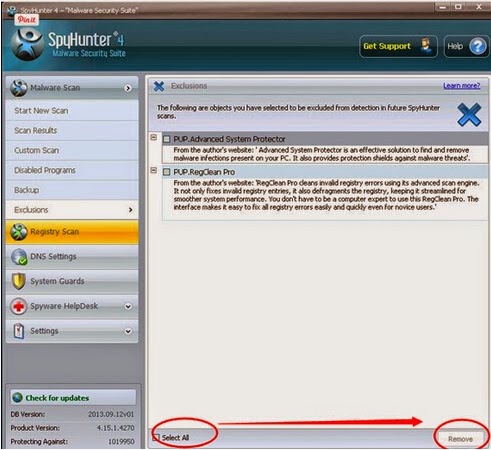
3. Click select all, then remove those threats from your computer completely.


No comments:
Post a Comment